This is the second article in my series on Desktop Linux Computing. You can read the original article here.
It's been well over a month since I install CentOS 6 on my mother-in-law's PC - and so far I've only had to make one service call - to install Skype.
Many people have asked me why I didn't install Fedora or Ubuntu. The answer is that I trust the stability of CentOS better, since it's an open source clone of Red Hat Enterprise.
When I was asked to install Skype on her laptop - apparently she had first researched and tried to do it herself - but because she was downloading the wrong package, CentOS wouldn't allow the install to continue.
One of the biggest problems normally present with family members' PCs is trying to find a balance between preventing the install of "crapware" and making sure the family member can still do everything they need to. I believe that by using CentOS 6, I've managed to find that balance.
I suspect that the next service call I receive will probably be to install OpenOffice - but I haven't received that call yet.
Stay Tuned! I will continue to post updates as they occur.
This Blog has Moved!
This blog is moving to
Thank you for visiting! Content will remain here for archival purposes.
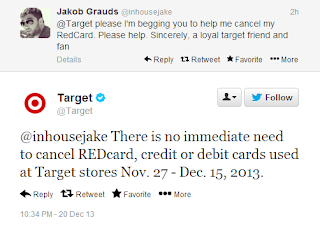
Target Customers' Credit Cards Now Available on Black Market
If you shopped at Target any time between November 27th and December 15th, cancel your card now. Target is giving very bad advice that you won't be held responsible for any fraudulent transactions. Even if caught, fraudulent transactions could quickly become a complete nightmare, resulting in the inability to pay bills or buy groceries.
As an update to my post Target Should Offer Free Credit Monitoring for Impacted Customers, customer credit cards have now been posted to the black market.
This is in complete contrast to statements previously made by Target claiming that there is no reason to cancel your credit cards.
Target is now claiming they will offer free credit monitoring services for everyone affected. If you shopped at Target during this time period with your credit or bank card, you should hold them to their word on this.
Target is also offering a 10% discount to customers who shop on the 20th and 21st. Personally I think this is a slap in the face to their customers, and many will have a hard time shopping and they probably won't have a credit card anymore, since they should cancel their card and have the bank issue a new one.
As an update to my post Target Should Offer Free Credit Monitoring for Impacted Customers, customer credit cards have now been posted to the black market.
This is in complete contrast to statements previously made by Target claiming that there is no reason to cancel your credit cards.
Target is now claiming they will offer free credit monitoring services for everyone affected. If you shopped at Target during this time period with your credit or bank card, you should hold them to their word on this.
Target Should Offer Free Credit Monitoring for Impacted Customers
In case you haven't heard, Target has been the victim of a massive network breach potentially impacting all credit card customers who shopped between November 27 and December 15 of this year, including Black Friday.
Normally when this happens, organizations try to make amends with their customers, often with free credit monitoring and identity theft protection for a year.
However, Target has chosen to take a potentially more damaging route (from a PR perspective), and simply direct customers to monitor their own accounts and request a free credit report.
Now it is understandable that Target is hesitant to do so, since credit monitoring services could potentially cost between $100 and $200 per person. Since 40 million customers are affected, this means Target would need to take a loss between $4 and $8 billion. According to MarketWatch Target's yearly profit has been approx. $20 billion. This would significantly impact their bottom line - but the potential loss of customers could be even more damaging.
Target - the ball is in your court. This could potentially make or break your company. Do you want to do the right thing and provide credit protection for customers? Or do you want to risk tarnishing the Target brand forever?
For historical reference, T.J. Maxx was forced to provide credit monitoring for customers.
Note: The blog author's family is most likely included in the list of affected customers.
Normally when this happens, organizations try to make amends with their customers, often with free credit monitoring and identity theft protection for a year.
However, Target has chosen to take a potentially more damaging route (from a PR perspective), and simply direct customers to monitor their own accounts and request a free credit report.
Now it is understandable that Target is hesitant to do so, since credit monitoring services could potentially cost between $100 and $200 per person. Since 40 million customers are affected, this means Target would need to take a loss between $4 and $8 billion. According to MarketWatch Target's yearly profit has been approx. $20 billion. This would significantly impact their bottom line - but the potential loss of customers could be even more damaging.
Target - the ball is in your court. This could potentially make or break your company. Do you want to do the right thing and provide credit protection for customers? Or do you want to risk tarnishing the Target brand forever?
For historical reference, T.J. Maxx was forced to provide credit monitoring for customers.
Note: The blog author's family is most likely included in the list of affected customers.
Security Explorer Trial Download
The following is external content provided as a free resource for blog readers.
 | Dell Security Explorer searches Windows servers to see who has rights to resources enterprise wide. It also provides management, recovery and reporting features at no extra cost.
Security Explorer centralizes permission management into one integrated console. Get your free trial. Request Free! |
Computer Code Could Potentially Infect Biological DNA via @SPTHvx
A research paper recently posted to Pastebin titled "Infection of biological DNA with digital Computer Code" claims a theoretical method which could be used by self-replicating malware to alter DNA.
The infection vector is somewhat similar to Stuxnet - infect computer systems then alter "fasta" files containing DNA information. When the altered files are synthesized, the computer code makes the transition into the biological realm as bacteria, where it continues to self replicate as a living organism.
I am by no means a microbiologist (and neither is the author of the paper), so I can't very easily confirm or deny the paper's contents. It sounds plausible, but then again it could have easily been created by modifying a paper generated by the CS Paper Generator.
The paper author is on twitter @SPTHvx.
Apparently a proof of concept virus is on SPTHvx's website.
Analysis of the proof of concept virus available at the following locations:
VirusTotal: https://www.virustotal.com/en/file/9aea60ee1796d711d166397a8407bef081a78849c6904ab9baf377155fb6630a/analysis/1387340634/
Anubis: http://anubis.iseclab.org/?action=result&task_id=17ea94fb60cbfe2a4ed4924b31e1ae344
The infection vector is somewhat similar to Stuxnet - infect computer systems then alter "fasta" files containing DNA information. When the altered files are synthesized, the computer code makes the transition into the biological realm as bacteria, where it continues to self replicate as a living organism.
I am by no means a microbiologist (and neither is the author of the paper), so I can't very easily confirm or deny the paper's contents. It sounds plausible, but then again it could have easily been created by modifying a paper generated by the CS Paper Generator.
The paper author is on twitter @SPTHvx.
Apparently a proof of concept virus is on SPTHvx's website.
Analysis of the proof of concept virus available at the following locations:
VirusTotal: https://www.virustotal.com/en/file/9aea60ee1796d711d166397a8407bef081a78849c6904ab9baf377155fb6630a/analysis/1387340634/
Anubis: http://anubis.iseclab.org/?action=result&task_id=17ea94fb60cbfe2a4ed4924b31e1ae344
The Essentials of Information Security Kit: Includes a Free PC Security Handbook - 2nd Edition eBook
The following is external content provided as a free resource for blog readers.
 | The Essentials of Information Security brings together the latest in information, coverage of important developments, and expert commentary to help with your Information Security related decisions. The following kit contents will help you get the most out of your Information Security research:
Request Free! |
The Modern Malware Review: Analysis of New and Evasive Malware in Live Enterprise Networks
The following is external content provided as a free resource for blog readers.
 | This review provides the first analysis of malware behavior that include not only analysis of how malware behaves on an infected host, but a full application level analysis of the infecting traffic as well as all traffic generated by the malware. Key Findings:
Request Free! |
10 Things Your Next Firewall Must Do
The following is external content provided as a free resource for blog readers.
 | The 10 Things Your Next Firewall Must Do outlines the latest capabilities that a firewall should possess and helps you learn how to choose a firewall that can safely enable your business in the ever-changing world of network security. By downloading this offer, you'll find an insight and practical advice on:
Request Free! |
Cybersecurity Imperatives: Reinvent Your Network Security With Palo Alto Networks®
The following is external content provided as a free resource for blog readers.
 | Read how a new modern security platform safely enables any technology and application.
Request Free! |
La Guía Definitiva Para La Evaluación De Los Firewalls Para Redes De Empresas
The following is external content provided as a free resource for blog readers.
 | Tome la decisión correcta sobre qué firewall es necesario para su negocio con La Guía para compradores de firewalls. Esta guía le da:
Request Free! |
Hidden Lynx Professional Hackers for Hire
The following is external content provided as a free resource for blog readers.
 | Symantec has identified a highly organized and sophisticated professional hacking group, made up of 50 to 100 individuals attacking a broad range of industries. Watch this recorded webinar and learn how:
Request Free! |
Macs, Malware and Security Myths
The following is external content provided as a free resource for blog readers.
 | Download this on-demand webinar and Security, Threat and Response Expert, Kevin Haley, will take a closer look at Macs, Malware and Security Myths:
Request Free! |
It's Time for Enterprises to Secure Mac Computers
The following is external content provided as a free resource for blog readers.
 | The Mac population has grown over the past few years as have Mac malware and development toolkits. Macs are also vulnerable to targeted attacks like APTs. For these reasons, CISOs should move beyond any lingering argument: It's time for Mac security in the enterprise. Request Free! |
Subscribe to:
Posts (Atom)